SSH tunneling otherwise called as port forwarding is a method of achieving connectivity to remote/blocked ports using SSH protocol.
In a scenario described below, you can make use of SSH tunneling.
Suppose you have, a desktop connects to a remote server which in turn has access to many other machines/devices on the remote network, and only SSH port is open for you to access through the firewalls. How will you connect to http service running on the remote network from your desktop?
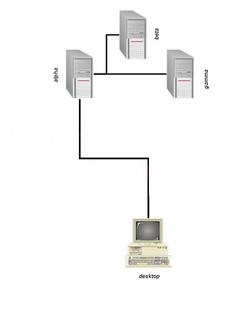
The answer is SSH port forwarding (tunneling). Let us look at how to do this. Assuming, Your desktop name is desktop(10.0.0.1), remote gateway server is alpha(10.0.0.1,192.168.1.1) and server which runs the service on remote network is beta(192.168.1.2).
Here desktop does not have direct access to beta or gamma. It has to access alpha for reaching those machines. Using SSH client a person using desktop can access alpha. Once he is logged in, he can access beta or gamma using SSH client which is available on alpha. We use putty (SSH client) for the sake of explanation. You can use any client which has the tunneling ability. Open putty and select SSH (default port 22) and give these details. Click on add and save the session.
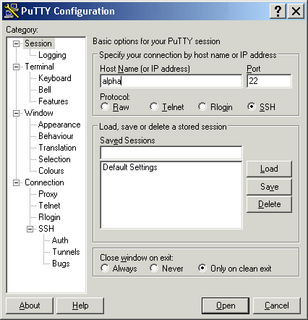
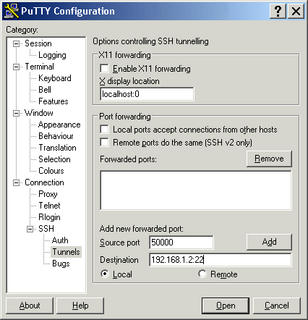
Note: you cannot use hostnames when you need to forward ports to the remote servers.
When you open this session, you will be prompted for username/passwords of Alpha. Once you are authenticated, the tunnel is set up to beta.
i.e Anything connecting on port 50000 on desktop will get forwarded to port 22 of beta. If you want to test this, open up another putty session to port 50000 of “localhost” as below. This will start a new SSH session from beta from your desktop.
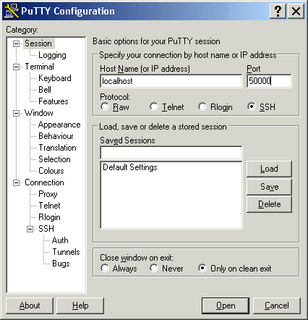
All communication sent across to beta is secured using encryption technology supported by SSH. You can forward to port 80 instead of port 22 (i.e 192.168.1.2:80), if you want to access the http server running on beta.
No comments:
Post a Comment